In this integration OAAM Server acts as a trusted partner application. The OAAM Server uses the Trusted authentication protocol (TAP) to communicate the authenticated username to OAM Server after it performs strong authentication and risk and fraud analysis. The OAM Server then redirects the user to the protected resource.
Pre-requisites
OAM 11.1.2.3 is installed and configured
OHS server is installed and configured
OAM Webgate agent on OHS is registered with OAM
Creating the OAAM Admin Users and OAAM Groups
Log in to weblogic console
Navigate to security realms –> myrealm –> Users and Groups –> Users
Create new user, click on new

Enter information and click ok

Now click on newly created user

Go to groups tab select all OAAM groups and click save

Import the OAAM base snapshot
Base snapshot is locate in ORACLE_HOME/oaam/init
File: oaam_base_snapshot.zip
Start OAAM Admin Server and log into OAAM admin console with new user. OAAM Admin console URL is
http://oaam_managed_server_host:oaam_admin_managed_server_port/oaam_admin
http://identity.oracleads.com:14200/oaam_admin
Go to System Snapshots and click load from file.

Select base snapshot file and click load

Click restore

Validate initial configuration of OAAM
Go to
http://host:port/oaam_server
http://identity.oracleads.com:14300/oaam_server
Enter any username click continue

Enter password as “test”and click enter

Click continue

Click continue

Enter security questions and answers (KBA) and click enter


If you are not able to validate OAAM initial configuration as in above, you must fix it before proceeding further.
Register the OAAM Server as a Partner Application to OAM
If OAAM is registered with Access Manager as a partner application, OAAM will then be able to communicate with Access Manager via the Trusted Authentication Protocol (TAP) to communicate the authenticated user name to the OAM Server after it performs strong authentication, risk, and fraud analysis, and the OAM Server owns the responsibility for redirecting to the protected resource.
If authentication is successful and the user has the appropriate profile registered, Oracle Adaptive Access Manager constructs the TAP token with the user name and sends it back to Access Manager. Access Manager asserts the token sent back. After asserting the token, Access Manager creates its cookie and continues the normal single-sign on flow in which it redirects the user to the protected resource.
Create a keystore directory
export IAM_ORACLE_HOME=/app/Middleware/Oracle_IDM1
mkdir -p $IAM_ORACLE_HOME/TAP/TapKeyStore
Run wlst.sh and connect to weblogic
cd $IAM_ORACLE_HOME/common/bin
./wlst.sh
wls:/offline> connect()
Please enter your username :weblogic
Please enter your password :
Please enter your server URL [t3://localhost:7001] :t3://identity.oracleads.com:7001
Run register command
registerThirdPartyTAPPartner(partnerName = “partnerName”, keystoreLocation=
“path to keystore”, password=”keystore password”, tapTokenVersion=”v2.0″,
tapScheme=”TAPScheme”, tapRedirectUrl=”OAAM login URL”)
registerThirdPartyTAPPartner(partnerName=”OAAMTAPPartner”,keystoreLocation=”/app/Middleware/Oracle_IDM1/TAP/TapKeyStore/mykeystore.jks”,password=”Oracle123″,tapTokenVersion=”v2.0″,tapScheme=”TAPScheme”,tapRedirectUrl=”http://identity.oracleads.com:14300/oaam_server/oamLoginPage.jsp”)

Adding a Password to the IAMSuiteAgent Profile
This profile is used by Oracle Adaptive Access Manager when integrating with Access Manager. When the IAMSuiteAgent profile is first created, it has no password. You must set a password before the profile can be used by Oracle Adaptive Access Manager for integration.
Log into oamconsole, click on agents

Click search, select IAMSuiteAgent, update Access Client Password and click on apply
Updating the Domain Agent Definition
Log into weblogic console
Navigate to security realms –> myrealm –> Providers , select IAMSuiteAgent
Go to provider specific tab, click on lock and edit. Update agent password
click on save and Activate Changes, restart weblogic servers
Verifying TAP Partner Registration
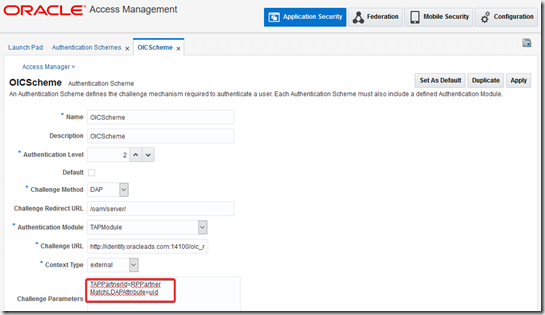
Login to oamconsole, go to Authentication Schemes
Open TAPScheme, edit as below and click apply

Launch Oracle Access Management tester
cd IAM_ORACLE_HOME/oam/server/tester/
java –jar oamtest.jar
validate as shown below
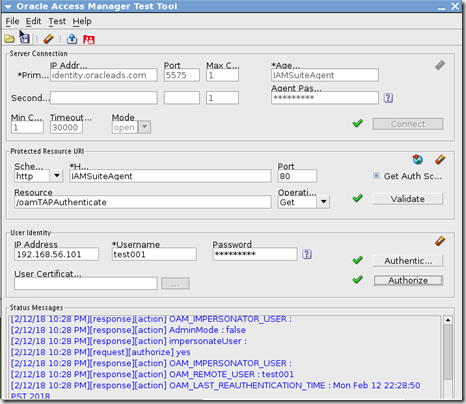
Set up TAP integration properties in OAAM
Make sure oaam managed server is running
mkdir -p temp/oaam_cli
cp –r OAAM_HOME/oaam/cli/. temp/oaam_cli
Edit temp/oaam_cli/conf/bharosa_properties/oaam_cli.properties below fields, rest fields keep as it is
oaam.adminserver.hostname=identity.oracleads.com
oaam.adminserver.port=7001
oaam.db.url=jdbc:oracle:thin:@identity.oracleads.com:1521:orcl
#keystore location entered in registerThirdPartyDAPPartner command
oaam.uio.oam.tap.keystoreFile=/app/Middleware/Oracle_IDM1/TAP/TapKeyStore/mykeystore.jks
#partnername entered in registerThirdPartyDAPPartner command
oaam.uio.oam.tap.partnername=OAAMTAPPartner
oaam.uio.oam.host=identity.oracleads.com
oaam.uio.oam.port=5575
oaam.uio.oam.webgate_id=IAMSuiteAgent
#communication security between OAAM and OAM
oaam.uio.oam.security.mode=1
oaam.csf.useMBeans=true
Save changes to oaam_cli.properties
Set Middleware home and Java home variables
export ORACLE_MW_HOME=/app/Middleware
export JAVA_HOME=/app/Middleware/jdk160_29
cd temp/oaam_cli/
chmod 777 setupOAMTapIntegration.sh
Run the OAAM setup integration script using the following command
./setupOAMTapIntegration.sh conf/bharosa_properties/oaam_cli.properties
Note: Enter the details on prompt. I have assigned all OAAM groups to default “”weblogic” user from weblogic console security realm. And used it as OAAM admin user





Configure Application Domain to use TAPScheme
Go to oam admin console, click on Application domains –> Application Domain –> Select Application Domain
Go to Authentication Policies and select Protected policy
 Change the authentication scheme to TAPScheme and click on apply.
Change the authentication scheme to TAPScheme and click on apply.

now go to Application Domain –> IAM Suite –> Authentication Policies –> Select “Protected HigherLevel Policy”. Make sure /oamTAPAuthenticate is protected by LDAPScheme
Testing
Make sure OHS, OAM and OAAM Managed servers are up and running.
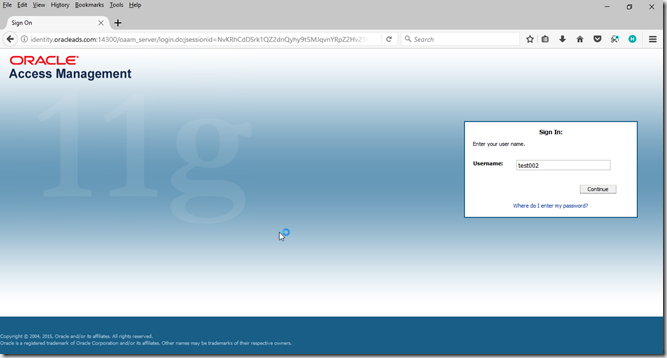
Hit the TAPScheme protected resource
http://identity.oracleads.com:7777
Enter username click on continue
Enter password click on enter

Click continue for registration
Click continue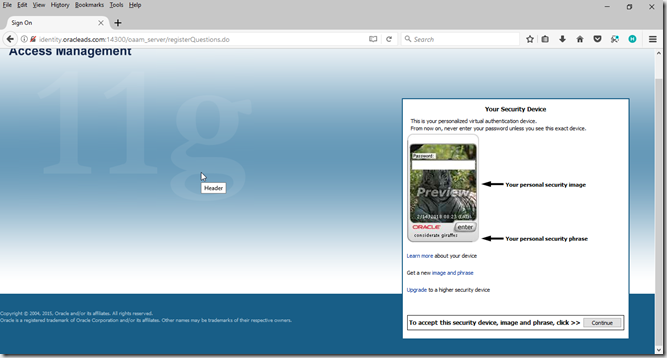 Enter security question and answers, click enter
Enter security question and answers, click enter

Demo: https://youtu.be/TIXXGWwM6oQ