Pre-requisite: Apply Bundle Patch 11.1.2.3.180116
How it works:
When NTLM and Kerberos authentications do not work with a browser (such as a non-domain attached browser), the OAM Server responds with an authorization error (403) and HTML content in the body of the response. By default, OAM displays an authorization error page with a Login button. The user needs to click the Login button in the customized page to invoke WNA fallback to FORM-based authentication. When user click on the Login button a cookie “OAM_WNA_OPT_OUT” is set by OAM. This cookie when set to true indicates the OAM server to challenge the user with FORM based authentication when the browser presenting the cookie is not supporting WNA authentication.
After below configuration is done, OAM will fallback to form authentication when validation of SPNEGO token fails. This use case is supported only when KerberosTokenAuthenticator plugin is used.
- Ensure that all WLS servers are stopped.
- Open and edit oam-config.xml, search for Version from top and increment the value.

- Search for WNAOptions, set the value of HandleNTLMResponse to FORM.

- Add below lines
Optional step
The OAM_WNA_OPT_OUT cookie is set as persistent cookie, by default. Configure it as a session cookie as follows
<Setting Name="IsOptOutPersistent" Type="xsd:boolean">false</Setting>
If you want to configure custom authorization error page when WNA fails. Set below under WNAOptions.
- Start all servers.
- You can use one of the below:
-
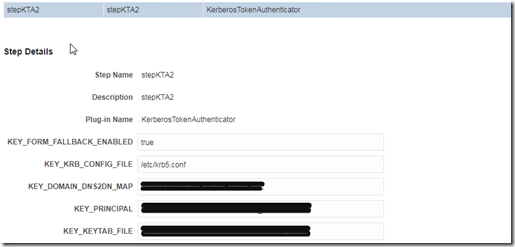
Modify KerberosPlugin from OAM Console –> Authentication Modules (or any other authentication module that you are using for kerberos authentication plugin).
Add a new step KTA (New step needs to be created because the newly added parameter is not present in edit). Set KEY_FORM_FALLBACK_ENABLED to true. Modify steps orchestration accordingly to use newly created KTA step.
OR
-
Edit KerberosTokenAuthenticator from OAM Console –> Plugins to set value for KEY_FORM_FALLBACK_ENABLED as true.

-
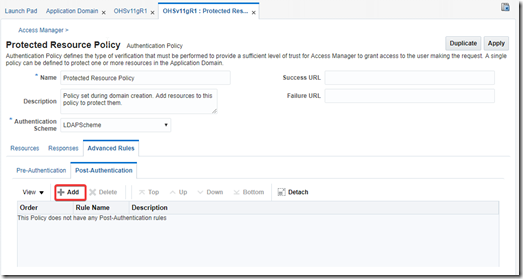
Configure pre-authentication rule to switch scheme to FORM based scheme, if OAM_WNA_OPT_OUT cookie is present in the request.
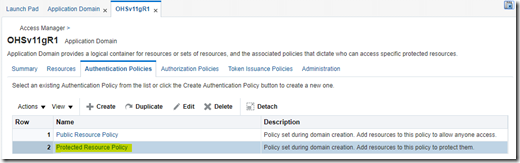
Go to Application Domain –> Authentication Policies –> Select WNA authentication policy –> Under Advanced Rules tab, Click on Pre-Authentication tab
Click Add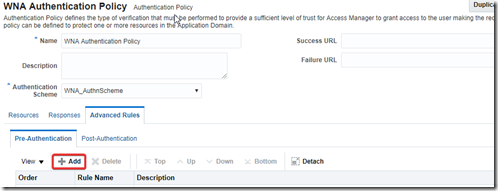

Rule: str(request.requestMap[‘Cookie’]).lower().find(‘oam_wna_opt_out=true’) >= 0
Click Add and Apply.
under <Setting Name="KerberosTokenAuthenticator" Type="htf:map">…………………
…….
under <Setting Name="initParameters" Type="htf:list">………………….
.
Add below:<Setting Name="4" Type="htf:map"><Setting Name="name" Type="xsd:string">KEY_FORM_FALLBACK_ENABLED</Setting><Setting Name="type" Type="xsd:string">string</Setting><Setting Name="value" Type="xsd:string"></Setting><Setting Name="length" Type="xsd:integer">256</Setting><Setting Name="globalUIOverride" Type="xsd:boolean">false</Setting><Setting Name="instanceOverride" Type="xsd:boolean">false</Setting><Setting Name="mandatory" Type="xsd:boolean">false</Setting></Setting>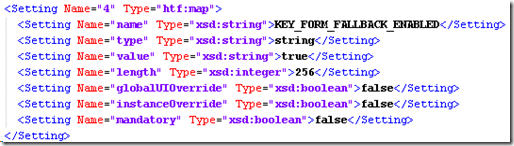
<Setting Name=”CustomOptOutPage” Type=”xsd:string”>/home/custom.html</
Setting>
Test: (From non domain machine browser)
- Request the resource protected by WNA authentication scheme
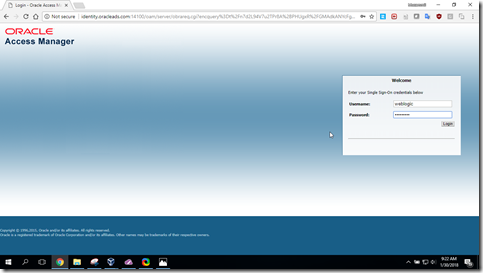
- User will be redirected authorization error page when WNA fails

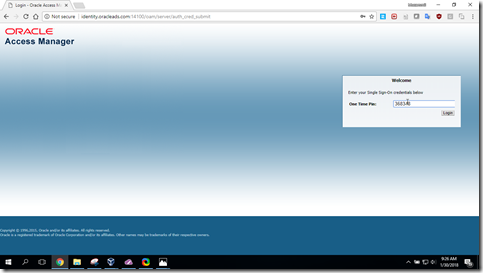
- Click on Login button (OAM_WNA_OPT_OUT cookie is set by OAM), user will be redirected to Form authentication as fall back (by evaluating pre authentication rule)
- Supply username and password for login